Post Event Analysis: Pulwama Attack
Background
A Suicide Vehicle borne IED (SVBIED) targeted a CRPF convoy traveling from Jammu to Srinagar on February 14. At least 44 troopers were killed in this attack which was subsequently claimed by the Pakistan backed regional militant group- Jaish e Mohammad (JeM). The assailant was reportedly a young Kashmiri local and was supposedly disenfranchised by the perceived excesses of the Indian security personnel deployed in the valley.
Why is the incident significant?
While the Kashmir valley and parts of Jammu have faced the scourge of militancy- local as well as those by Pakistan backed militant groups for decades, the Pulwama attack remained significant for the following reasons: -
Unprecedented Modus Operandi (MO)
Despite a prolonged militancy witnessed in the region, SVBIED attack remains a remote phenomenon. In this context, the last known SVBIED attack in Kashmir was recorded on November 2, 2005 in Nowgam which reportedly killed three security personnel and six civilians. This incident was preceded by a similar SVBIED attack targeting the Jammu and Kashmir Legislative Assembly in 2001 by JeM in which at least 41 people, including assailants were reportedly killed. The rarity of such incidents coupled with prevalence of other less sophisticated MO’s like shooting and low intensity IED’s have also resulted in a security posture more adept at dealing with the latter.
Complacency
Indian Security forces operating in the Kashmir valley operate under a comprehensive three tier security grid involving border management and security, operations in the hinterlands and finally security of the major locales like Srinagar. These tiers are backed by a supposedly robust multi-agency intelligence setup aimed at facilitating operations. Given the high rate of intelligence inputs that flows through each of these agencies and the uphill task of processing each of these inputs makes way for compliance to set in. This is especially more likely in the event of prolonged periods of status quo, devoid of a major attack.
In case of Pulwama, while unconfirmed reports indicated of a high probability of an attack targeting security personnel between Pampore and Pulama, failure to act upon these, either by virtue of complacency or sheer scale of other intelligence inputs which remain unaddressed further magnified the impact of the attack.
Lack of adherence to Standard Operating Procedures and Loopholes
As per revised protocols adopted by the security forces operating in the Kashmir valley from 2012, the authorised strength of a convoy was between 30-40 vehicles. In case of the attack, the convoy comprised of roughly 78 vehicles (almost double of the authorised strength) with more than 2500 personnel traveling in it. Reports also indicate of a far larger convoy movement in the preceding week which reportedly had at least 90 vehicles, along the same route and which managed to reach its intended destination without any event. It is this very factor, combined with the fact that no convoy movement had taken place in the preceding two days due to inclement weather conditions that may have potentially led to movement of such a large convoy. Moreover, the frequency of such movement, including the predictable travel pattern, speed of convoys and a general understanding of the response mechanisms only made the convoy predictable and thus easier to target.
Secondly, a lot of emphasis was attributed to ‘faulty’ road opening party (ROP) procedures. While the current protocol adopted by the Army as well as the Central Armed Police Forces (CAPF’s) operating in the Kashmir security, operations in the hinterlands and finally security of the major locales like Srinagar. These tiers are backed by a supposedly robust multi-agency intelligence setup aimed at facilitating operations. Given the high rate of intelligence inputs that flows through each of these agencies and the uphill task of processing each of these inputs makes way for compliance to set in. This is especially more likely in the event of prolonged periods of status quo, devoid of a major attack.
In case of Pulwama, while unconfirmed reports indicated of a high probability of an attack targeting security personnel between Pampore and Pulama, failure to act upon these, either by virtue of complacency or sheer scale of other intelligence inputs which remain unaddressed further magnified the impact of the attack.
Prevalence of IED attacks in Kashmir
There has been a notable surge in use of IED’s in the Kashmir valley with ever improving MO’s. The militant groups have shown tendencies to be adaptive as well as adoptive. In the latter half of 2016, the ‘command-wire’ technique was prevalent, which security agencies linked to the successes witnessed by Left wing extremists- Naxals in their areas of operation in central and eastern India against security forces. While effective measures were devised and fielded to counter this strategy, reports now indicate of increasing preference for remote triggering mechanisms, including use of anti-theft remote alarms, mobile phones, radio sets among others used to trigger the IED. The effectiveness of these triggering mechanisms is only magnified further by the use of locally available explosives in majority of the cases and availability of other explosive materials like ammonium nitrate in certain cases. Use of military grade explosives like RDX, PETN and TNT also remains prevalent, albeit rare, especially in Kashmir. This can primarily be attributed to comprehensive security operations over a prolonged period of time which has aimed at disrupting the supply chain of these explosives in the region.
Finally, the target of these attacks have primarily been security personnel as well as entities perceived to be siding with the government or facilitating security operations. Cases of mistaken identity and collateral have also been recorded over the preceding months.
Analysis of the MO used in Pulwama
While the Pulwama attack continues to remain under investigation by the National Investigation Agency (NIA), the critical details including the type of explosives used, the triggering mechanism and the logistics employed to move the explosives to the assembly point before deployment remains to be ascertained.
That being said, as per preliminary reports and field visuals, including recovery of what could potentially have been a jerrycan from the blast site hints towards the likelihood of a combination of explosives including RDX and explosives used for quarrying. This view is further bolstered by the fact that a sizable amount of explosive were readily available in the vicinity owing to the ongoing work for broadening the Jammu-Srinagar route into a four lane highway to address the traffic congestion issues frequently observed in this region. Moreover, the Awantipora bypass, which happens to be approximately 3.34 km stretch and which lies approximately 13 km south of Lethipora, (scene of attack) could gives further credence to the use of explosives like supergel-90 which is typically used in these projects.
Secondly, while estimates continue to vary with respect to the quantity of explosives used, the extent of damage hints towards a possibility of roughly 30-40 kg of RDX. Estimates also hint towards the possibility of the explosives being smuggled into the state in small batches via established smuggling routes in Punjab or by those militants crossing over into India from Pakistan. However, in the absence of any official clarification on the issue and ongoing investigation, the supply chain employed is only a matter of speculation.
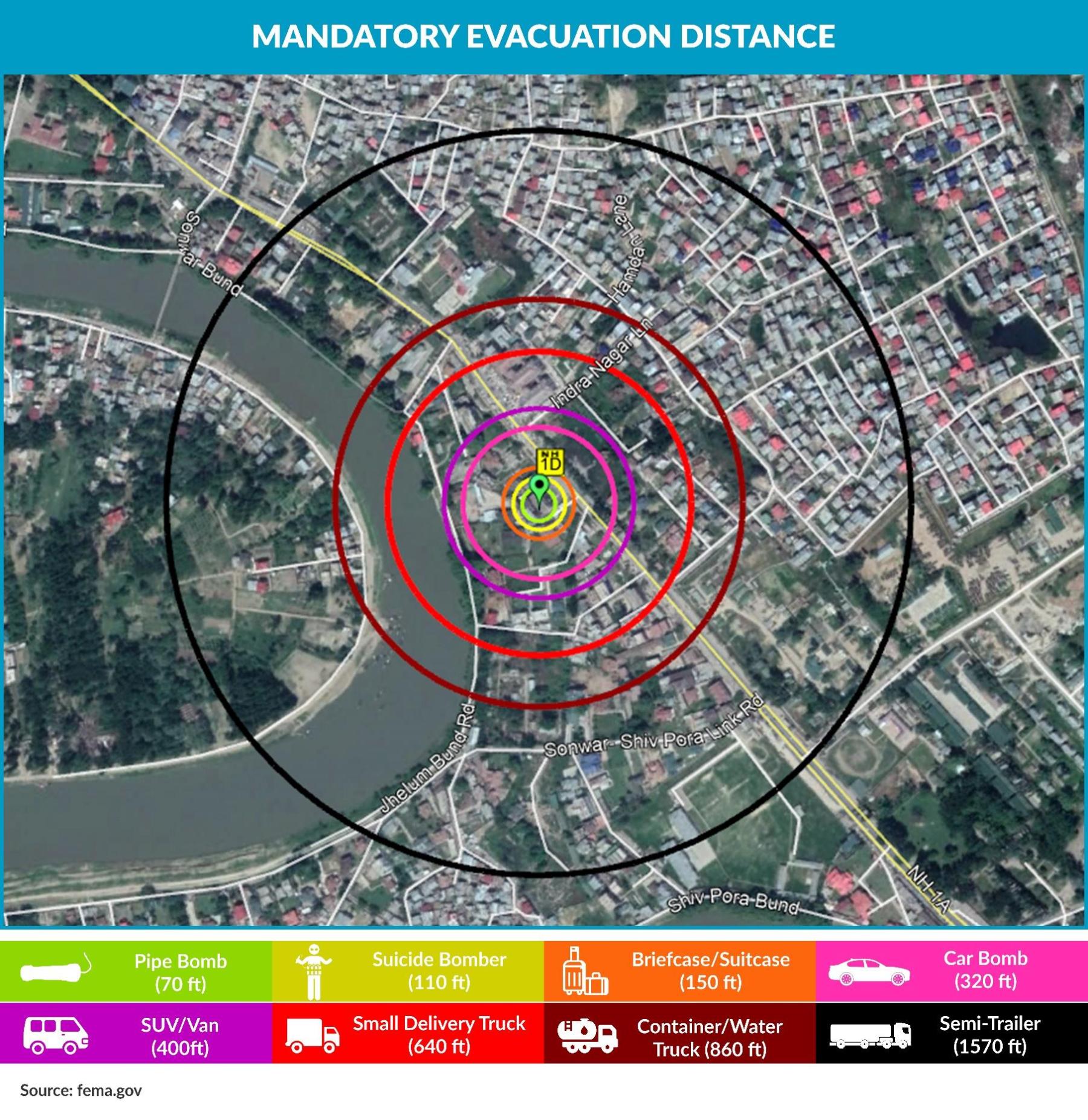
What to expect?
Despite the punitive airstrikes in Pakistan’s Balakot region by the Indian Air Force, the likelihood of additional attacks by the JeM remains likely to continue. While the battle damage assessment continues to vary, the group, over the years, is known to have succeeded in dispersing its installations and training facilities across Pakistan and parts of Afghanistan. It thus remains likely that the the latest airstrike had a limited impact on the operational capabilities of this group.
Moreover, given the close ties between JeM and the Taliban in Afghanistan, which has not only effectively carried out such attacks, but has adapted some tactics against Afghan and US led coalition forces in country, some transference of these MO’s remains likely. This view is further bolstered by the adaptive and adoptive strategy demonstrated by these groups in the preceding section. Unconfirmed reports quoting senior Afghan security officials also indicate of involvement of JeM cadres in the latest Shorab Airbase in Helmand Province along the Afghan-Pakistan border hints towards a possible cooperation between the two groups. It also hints towards the operational experience these groups are likely to gain transference of which remains more or less certain in Kashmir over the coming months.
If this is confirmed, the likelihood of even more sophisticated MO’s, including potential use of explosive formed penetrators (EFP’s) alongside relatively increased number and frequency of IED/VBIED/SVBIED attacks remains likely to be recorded over the coming months.


https://www.waste-ndc.pro/community/profile/tressa79906983/
1 year agohttps://ternopil.pp.ua/
1 year agoJamestep
1 year ago